Internet service providers are the the way we connect to the internet. For the most part they offer us unfettered access to anything online.
The problem: there are a lot of unscrupulous people on the internet alongside us, many happy to send spam, infect computers with viruses, steal your banking details and even your identity just to make a quick buck. Should our ISPs change their open stance and aim to protect us from such threats?
Botnets
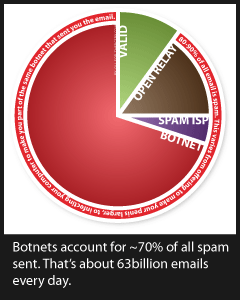
As I mused in my last post, every day some 63 billion spam emails come from groups of infected computers known as botnets. These computers are usually home/company desktop machines that have been infected with a trojan, allowing the owner of the botnet to control them in any way they wish.
Botnets account for most online illegal activity. They send viruses to swell their ranks and can flood servers, even countries with massive amounts of network traffic, effectively cutting off internet communications to or from the target.
The scale of the problem is immense. Vint Cerf thinks that 25% (150,000,000) of all online computers are part of a botnet. Some people put this figure a lot closer to 50%.
As Aaron Kornblum from Microsoft said last year, botnets are the most dangerous threat to online security we face, mainly because of the power a botnet owner wields.
The only ways to destroy a botnet are: tracing, catching and imprisoning its controller or disinfecting all the computers that make it up. Neither have proven particularly successful so far.
Isn’t Windows to blame?
You could argue that. The popularity of Windows has seen it sustain a massive influx of viruses and worms hell-bent on gaining control over all its users’ computers. Microsoft have been slow to fix problems in the past but equally, no other company on the planet has to play the security game like they have to. I’m not saying they’re blameless, just blaming them won’t fix the problem.
I dream that one day, when we’re all using Linux that botnets will no longer be an issue but the glass-half-empty guy in me fears that the writers of this malware will just target that instead. Perhaps the glass is too big?
You also have to remember that one of the main ways computers get infected with this stuff is through users’ ignorance. They trust a website download or email attachment and run it, not knowing it will infect their computer and hand control over to a botnet.
ISP neutrality
The recent debates over net neutrality may apply to this question. The core argument with neutrality is that ISPs should not discriminate against traffic based on where it comes from. For example pro-neutrality people say your ISP should not be able to slow or block access to one service provider (eg: Yahoo!) in favour of another (eg: Google).
But the fact of the matter is ISPs have been doing similar things to this for some time. My ISP cuts off any bittorrent activity for 14hours of every day. They seem happy to block things when it suits them.
Many email providers also have virus scanners on their servers so customers can have some level of assurance that what they download isn’t harmful. Protection isn’t guaranteed but it’s a level of security that does stop thousands more computers joining botnets.
ISPs can very easily detect which of their customers are infected with trojans and are sending out or hosting spam or viruses. It’s just a case of traffic profiling, which, as I’ve already said, a great many do to protect them from peer-to-peer file-sharing users annihilating their bandwidth.
What they should realise is hosting botnets also consumes their network’s bandwidth. If they blocked botnet activity and notified their infected customers, they would very quickly see a drop in illegal activity originating from their networks.
But in order to have a meaningful impact on botnets, changes would have to be legislated and global.
So what am I suggesting?
The largest botnets are concentrated inside the USA alongside several European countries on Spamhaus’s top-10 list.
These aren’t mythical WMDs; they are droves of mindless computers willing to do anything the controller wants them to do and when they focus their collective power, they’re really quite dangerous.
If ISPs in the EU and US could be made to do the following things, a good 80-90% of botnet computers could be removed from active duty as well as protecting their users from most phishing attempts and botnet “recruitment drives”:
-
Block direct mail-server contact
In order to send spam, botnet computers usually connect to one of a list of mail servers. If ISPs stopped the access to these servers and forced the users to phone up (or register online) and say “I want to use mail.mydomain.com for my email address oli@mydomain.com”, they would cut 99% of spam coming from them overnight.
It would be initially painful for users but done globally, they would be grateful for the decrease in spam.
-
Block internet access to infected sites/computers
The main propagation method of botnets entails users downloading dodgy files from corrupted/hacked web servers or botnet computers. There are published lists of reports of which computers are afflicted, so this could very quickly stop people getting access to the files that will infect them and therefore stunt the growth of botnets.
Existing DNS services like OpenDNS provide blocking capabilities like this and I can’t see it being that stressful on users or the ISP to implement this.
-
Block internet access from infected customers
Most people don’t give a crap about their computers security. If the computer still works for what they want to do, chances are a bit of malware will never be actively removed. With the ability to detect which customers are infected, ISPs should not just notify them but completely block their access to online services until computers on their network are safe.
This could be implemented by redirecting all http traffic through to an internal server that displays a message saying they’ve been blocked, tell them how severe the problem really is and then offer them some free clean-up tools.
The third point would cause people the most problems and probably a butt-load of technical support calls but if every ISP in the US and EU followed those steps (or was made to), botnets could be neutered to a level where they’re barely noticeable, let alone effective.
Some ISPs offer notifications but my experience with this is when my housemate’s computer had some crapware, NTL (my ISP, then) sent an email to an NTL mailbox that I never ever checked. We noticed there was a problem when the connection came crawling to a halt as the trojan saturated the upstream by sending too many emails.
These are things we all need before the internet explodes under the weight of the zombies (botnet computers). As internet connections get faster and faster, the damage each zombie does multiplies. This is something that must happen today, not tomorrow.